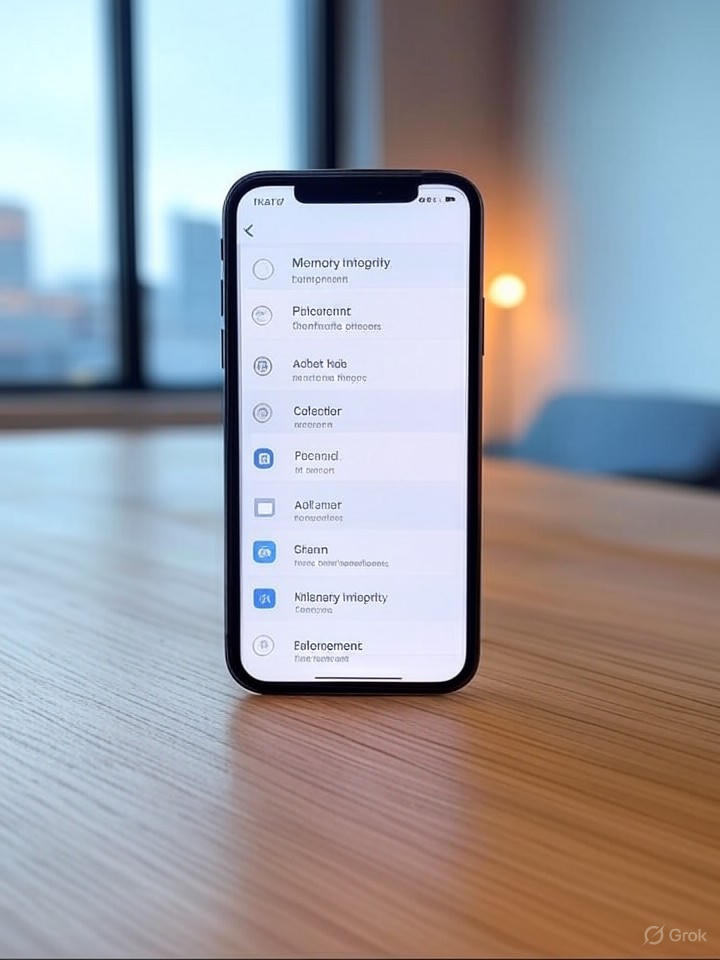
In a decision that highlights Apple’s continuous commitment to strengthen the confidentiality of users in the middle of cyber-menua, the company has discreetly introduced what experts call one of its most pragmatic security improvements to date. This feature, deployed without much fanfare in the recent software updates, aims to strengthen the defenses of the iPhone against sophisticated spy software and memory -based exploits, potentially defining a new reference for mobile security.
The details emerging from industry reports underline how this update incorporates advanced memory protection mechanisms, which makes it more difficult for malicious actors to compromise the integrity of devices. By taking advantage of the hardware synergies of hardware software unique to Apple ecosystem, the function applies more strict controls on how applications access and handle the memory of the system, a common vector for zero-day attacks.
Improve memory safety in real time
This innovation is based on Apple history of proactive security measures, such as those observed in previous iOS iterations. According to a report of 9TO5MACThe functionality was “quietly shipped” as part of the last iOS deployment, even catching analysts experienced by surprise with its discreet deployment. The initiates note that it deals with vulnerabilities that have tormented not only iphones, but the wider market of smartphones, where the corruption bugs have allowed high -level violations.
Practical implications are deep for business users and high -risk individuals, such as journalists or managers, who are faced with targeted Spymetric software campaigns. By implementing what Apple describes as the application of memory integrity, the system monitors and dynamically isolates suspicious memory operations, reducing the effectiveness of exploits based on the crushing of critical data structures.
A strategic change in Apple’s security philosophy
Comparisons with past features, such as the locking mode introduced in iOS 16, reveal an Apple model prioritity of conviviality in parallel with robust protection. Techradar, in his analysis at TechradarPraises this as “the most important upgrading of memory security in the history of consumer operating systems”, emphasizing its potential to thwart mercenary Spyware companies like NSO Group.
For developers, this means adapting applications to comply with improved memory guarantees, which could initially set up integration challenges but ultimately raise the overall security posture of the ecosystem of the App Store. Industry observers speculate that this silent liberation strategy allows Apple to collect real data on functionality performance before a broader promotion, minimizing disturbances.
Implications for competitors and regulators
The deployment coincides with Apple’s thrust for greater independence from fleas, as detailed earlier 9to5mac coverwhere personalized silicon like the MS processors allows such fine commands. This could put pressure on rivals like Google and Samsung to speed up their own safety innovations, which could reshape standards through Android-IOS division.
Regulatory organizations, including those of the EU examining Apple’s privacy practices, can consider this positively as proof of real protection efforts. However, questions persist on transparency – why the discreet introduction? Some experts suggest that it is to avoid alerting threat actors prematurely, allowing the functionality to integrate deeply before emerging the countermeasures.
Looking: adoption and challenges
The adoption rates will be essential, with the first indicators of beta testers showing transparent integration on devices such as the iPhone 17 series. Macworld Note that even if it complicates the development of spy software, it does not completely eliminate risks, urging users to combine it with best practices such as regular updates and prudent application authorizations.
As cybermenaces evolve, this characteristic illustrates Apple’s methodical approach to security, mixing innovation with pragmatism. For the initiates of the industry, it signals a maturation phase where subtle improvements offer disproportionate impacts, strengthening Apple’s position in a world where data protection is essential. Future iterations could extend this to Mac and iPad lines, more unifying the defenses of the ecosystem.