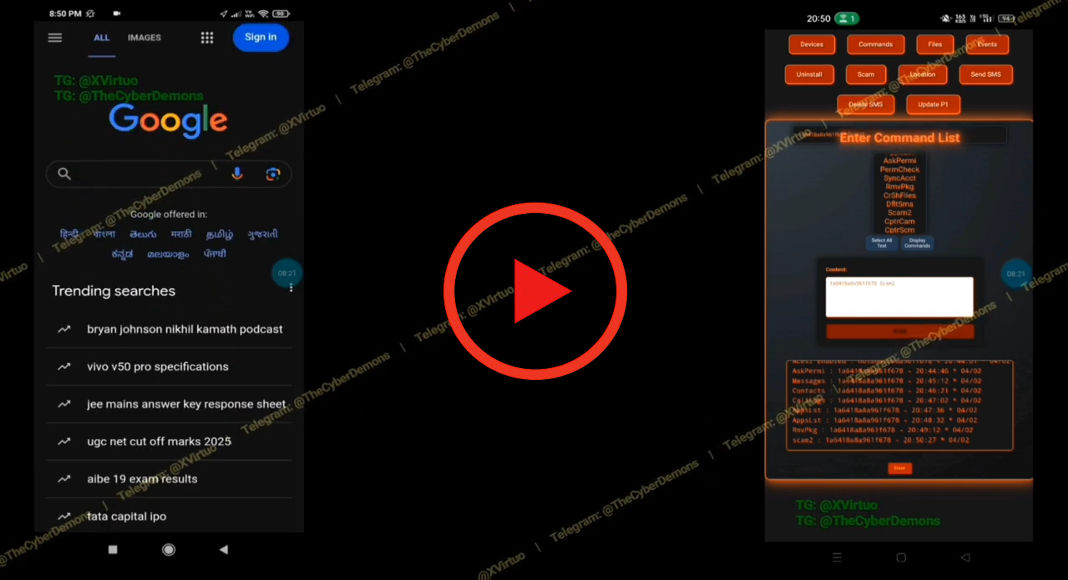
A new Trojan of Trojan of Android Distance (RAT) presented as completely undetectable appeared publicly on Github, aroused serious concerns among cybersecurity researchers.
Donated to bypass the advanced restrictions of authorization and processes in the background, in particular in the Chinese ROMs such as MIUI and EMUI, this rat represents one of the most sophisticated public threats ever observed.
By focusing on persistence, encrypted communications and the lack of visibility on antivirus software, researchers warn that malware could feed a new wave of ransomware and identifier flight campaigns.
Advanced injection and escape of authorizations
The rat incorporates a multilayer droppings which integrates its payload into legitimate files. Android Applications, allowing without distrust users to install APK compromises.
Unlike conventional rats, it is designed to defeat automatic start restrictions, background application controls and aggressive battery optimization systems that are largely found in personalized Android Roms.
Once installed, he silently elevates his privileges, automatically agreeing with complete accessibility, notification and administration rights thanks to the execution of controlled scripts. This effectively neutralizes the user’s authorization model, allowing furtive execution immediately after infection.
Encryption plays a central role in its design. The command and control communication (C2) uses the AES-128-C encryption with PKCS filling, ensuring that all the transmitted data remains protected even during an in-depth inspection of the packets.
According to the developer’s documentation, the configuration, including the C2 address, is fully masked, thus preventing any exhibition during the decompilation of the APK or the reverse engineering.
An additional anti-emulator module checks the material parameters before execution, thus blocking operation in the sandbox environments used by analysts.
Complete compromise of devices and surveillance capacity
Once active, the RAT takes total control of the device, reflecting the functionality of espion software of commercial quality. It can record and delete call logs, take or intercept vocal calls and handle SMS messages, including reading OTPs and usurping the sender information.
Thanks to its integrated striking recorder, the malware captures each offline and online strike, targeting the identification information for banking applications, cryptographic wallets, messaging customers and two -factor authentication tools.
Malware also incorporates several data exfiltration features, including live screenshots, access to the front and rear cameras, audio and video recording and the diversion of the clipboard, which replaces the cryptocurrency wallet addresses with those of the attacker.
Its ransomware component adds an additional danger by encrypting the files on the storage partitions and locking the interface of the device until a ransom request is satisfied.
Meanwhile, the attacker can lock, unlock or even erase the entire device remotely, transforming the rat of spy software into a destructive payload.
The inclusion of usurped notifications, cloned application connection pages and automated phishing prompts adds a layer of social engineering to the infection chain, allowing the theft of real -time identifiers.
Persistence, stealth and public exhibition
Rat persistence mechanisms are designed for longevity. It minimizes the use of system resources by performing a background process which consumes a negligible quantity of CPU and battery.
In “frozen mode”, its network traffic falls at less than 3 MB per day, which makes detection by the network monitors extremely difficult. Hidden icons and delayed task planning prevent suspicion of users, while false system of system dialog are used to make safety applications and Play Protect manually plant.
The most alarming is perhaps its accessibility: the striker’s interface is entirely based on the web, requiring any specialized infrastructure or port redirection. An operator can run total control orders from any standard browser on Android, Linux or Windows devices.
By making such a powerful toolbox available free online, its developers have effectively lowered the barriers to the entry for the deployment of industrial quality espionage operations.
The public release of this Fud Android Rat underlines the growing abuse of open source standards for the distribution of armed tools.
Security analysts are now requiring the immediate abolition of the project and increased monitoring of the publication of malware on Github in order to prevent a new global exploitation of Android.
Find this story interesting! Follow us on Google News ,, Linkedin And X To get more instant updates