Fantasy Hub: Android RAT, sold in Russia, offers comprehensive device spying as MaaS
November 11, 2025
Researchers discovered Fantasy Hub, a Russian Android MaaS RAT that allows attackers to spy, steal data, and control devices via Telegram.
Zimperium researchers discovered Fantasy Hub, an Android RAT sold in Russia and offered as Malware-as-a-Service, enabling spying, device control and data theft via Telegram.
The malware allows operators to take control of infected devices, collecting SMS messages, contacts, call logs, images and videos. The malicious code also allows attackers to intercept, respond to, and delete incoming notifications, among other functionalities.
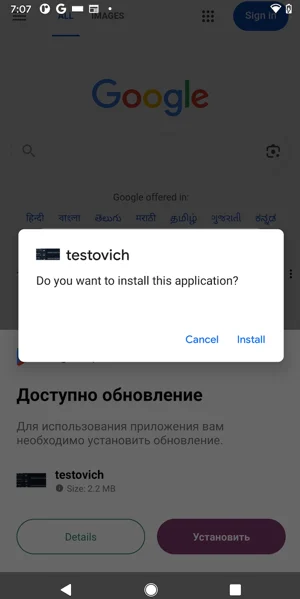
The authors advertise the spyware’s capabilities online and link to a bot that manages paid subscriptions and access to builders, as well as step-by-step guides (and a video) for creating fake Google Play pages and evading detection.
Attackers use it to target banks, displaying fake login windows for Alfa, PSB, Tbank and Sber in order to steal credentials.
“Fantasy Hub is not a single basic kit: it is a MaaS product with vendor documentation, videos, and a bot-driven subscription model that helps novice attackers by providing a low barrier to entry. read it report published by Zimperium. “Because it targets financial workflows (fake windows for banks) and abuses the SMS handler role (to intercept 2-factor SMS messages), it poses a direct threat to enterprise customers using BYOD and to any organization whose employees rely on mobile banking or sensitive mobile applications.”
The Command and Control panel displays subscription duration, device online/offline status, make/model, last update, user ID, and SIM slot information. Sellers document Telegram integration (bots, chat IDs, tokens) to receive alerts and provide a comprehensive guide to manage victims, controls for SMS, contacts, calls, push notifications and more, allowing buyers to remotely operate and monitor compromised devices.
Malware analysis reveals the use of a native dropper inside a metamask_loader library that decrypts an embedded element metadata.dat with a custom XOR (36 byte key), decompresses it (gzip/zlib) and writes the payload to disk. This trick allows you to hide static flags until runtime. Fantasy Hub abuses the default SMS manager role to get extended permissions (SMS, contacts, camera, files) in one step. The dropper presents itself as a Google Play update and checks for rooting to escape scanning. For spying, it uses WebRTC to stream live camera/microphone feeds to the C2 (after downloading the required libraries), displaying a small “Live Stream Active” indicator while streaming.
Fantasy Hub combines native droppers, WebRTC live streaming, and SMS handler abuse with social engineering and fake app tactics, making it far more dangerous than typical piggyback Trojans, especially in BYOD and consumer contexts where trust in app stores lulls users into a false sense of security.
“The rapid rise of Malware-as-a-Service (MaaS) operations like Fantasy Hub shows how easily attackers can use legitimate Android components to completely compromise the device. Unlike older banking Trojans that rely solely on overlays, Fantasy Hub integrates native droppers, WebRTC-based live streaming, and abuse of the SMS handler role to exfiltrate data and impersonate legitimate applications in real-time.” concludes the report. “This mix of social engineering and deep system control makes it particularly dangerous in BYOD and consumer-facing environments where trust in app stores is assumed. »
Follow me on Twitter: @businessofsecurity And Facebook And Mastodon
(Security Affairs – hacking, MaaS)