Cybersecurity researchers at Unit 42 discovered a sophisticated Android spyware campaign that exploited a previously unknown zero-day vulnerability in Samsung Galaxy devices.
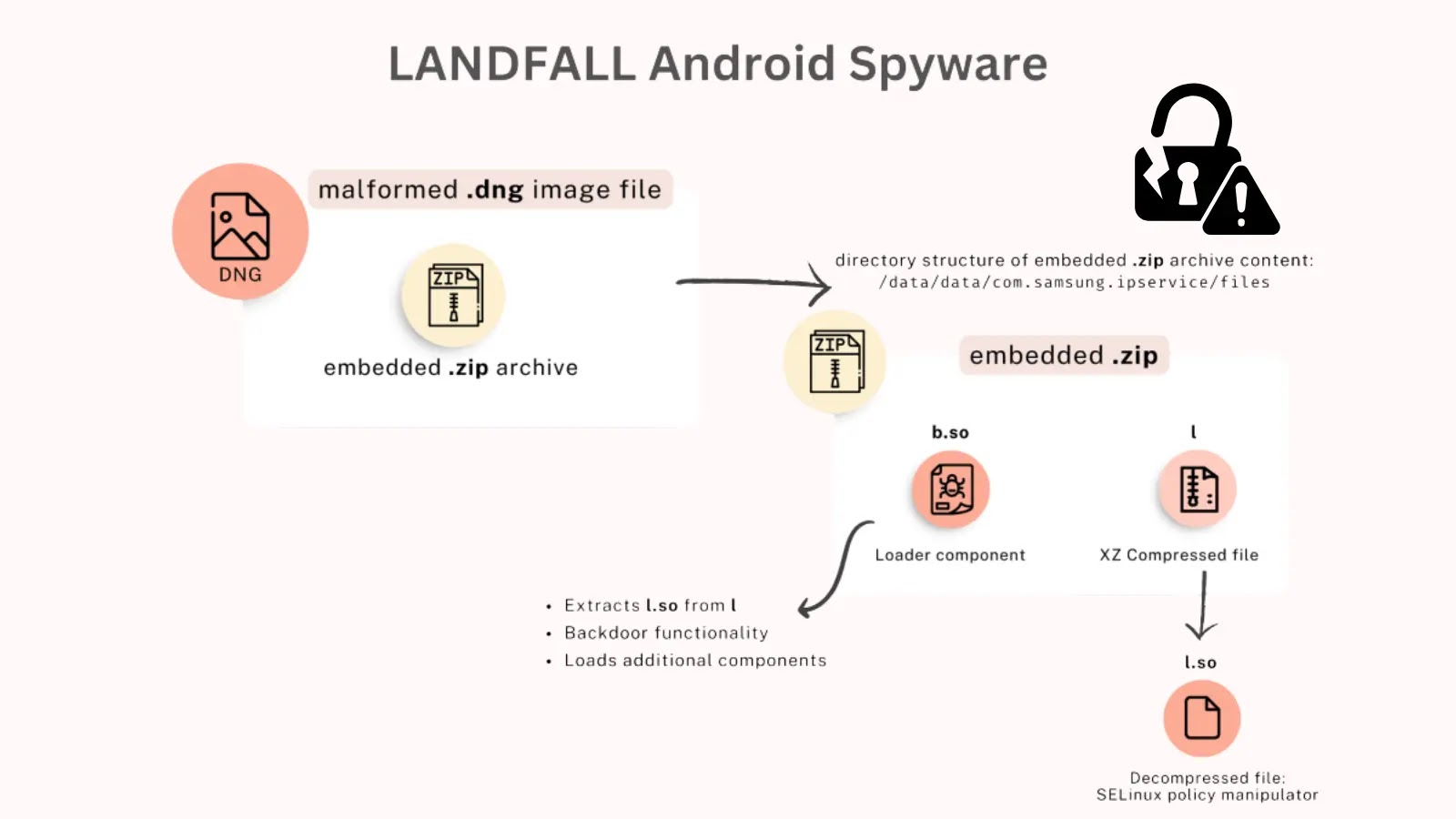
The malware, dubbed LANDFALL, exploited a critical vulnerability in Samsung’s image processing library to provide commercial-grade surveillance capabilities via malicious image files sent via WhatsApp.
The LANDFALL campaign exploited CVE-2025-21042a zero-day vulnerability in Samsung’s Android image processing library that was not patched until April 2025.
The attackers embedded the spyware in malformed DNG (Digital Negative) image files, which were delivered to targets via WhatsApp messages.
The exploitation method closely resembles a similar attack chain discovered targeting Apple iOS devices in August 2025, highlighting a broader pattern of DNG image processing vulnerabilities being used as weapons on mobile platforms.
Unit 42’s discovery came during its investigation into iOS exploit chains when it identified several suspicious DNG files uploaded to VirusTotal throughout 2024 and early 2025.
File names, such as “WhatsApp Image 2025-02-10 at 4.54.17 PM.jpeg” and “IMG-20240723-WA0000.jpg”, strongly suggest that the malware was distributed via WhatsApp’s messaging platform. Importantly, the researchers did not find any vulnerabilities in WhatsApp itself: the app was simply used as a distribution mechanism.
Samsung 0-Day Vulnerability
LANDFALL is specially designed to target Samsung Galaxy devices, including the S22, S23, and S24 series, as well as the Z Fold4 and Z Flip4 models.
The b.so component of LANDFALL communicates with its C2 server over HTTPS using a non-standard ephemeral TCP port.
The spyware offers extensive monitoring capabilities, including microphone recording, location tracking, collecting call logs, and extracting photos, contacts, and SMS messages. Its modular architecture suggests it could download additional components to expand its functionality.
The malware loading component, internally called “Bridge Head”, contains sophisticated evasion techniques to avoid detection by security tools and debugging frameworks.
The analysis revealed that the spyware could manipulate Android’s SELinux security policies to maintain elevated permissions and establish persistence on infected devices.
Evidence indicates that LANDFALL was deployed as part of targeted intrusion activities in the Middle East, with potential victims identified in Iraq, Iran, Turkey and Morocco.
The campaign’s infrastructure and business models share similarities with commercial spyware operations associated with private sector offensive actors (PSOAs), entities that develop and sell surveillance tools to government customers.
Researchers noted potential links to the Stealth Falcon threat group and possible links to the Variston spyware, which reportedly operated from Barcelona before ceasing operations in early 2025.
Configuration of the b.so file is handled via a combination of hardcoded defaults and an encrypted JSON object embedded within itself.
The “Bridge Head” naming convention used by LANDFALL matches the terminology used by several known commercial spyware vendors, including NSO Group and Variston.
Timeline and current status
Unit 42 is tracking this activity as CL-UNK-1054 and continues to investigate the scope and attribution of the campaign. Palo Alto Networks customers receive protection through Advanced WildFire, Advanced URL Filtering, Advanced DNS Security, and Advanced Threat Prevention products, which have been updated to detect LANDFALL-related indicators.
The first samples of LANDFALL appeared in July 2024, months before Samsung patched the vulnerability in April 2025.
In September 2025, Samsung patched an additional related vulnerability, CVE-2025-21043, further protecting users from similar attack vectors. Samsung users who have applied security updates since April 2025 are no longer exposed to this specific exploit.
Follow us on Google News, LinkedInAnd X to get instant updates and set GBH as preferred source in Google.