A sophisticated Android Troy Banking campaign taking advantage of a malware manager application has accumulated more than 220,000 downloads on the Google Play Store before it deleted.
Nicknamed Anatsa (also known as Teabot), malware targets global financial institutions thanks to a process of infection in several stages. It deploys false connection overlays and abuse accessibility services to steal identification information and execute unauthorized transactions.
Anatsa attack chain
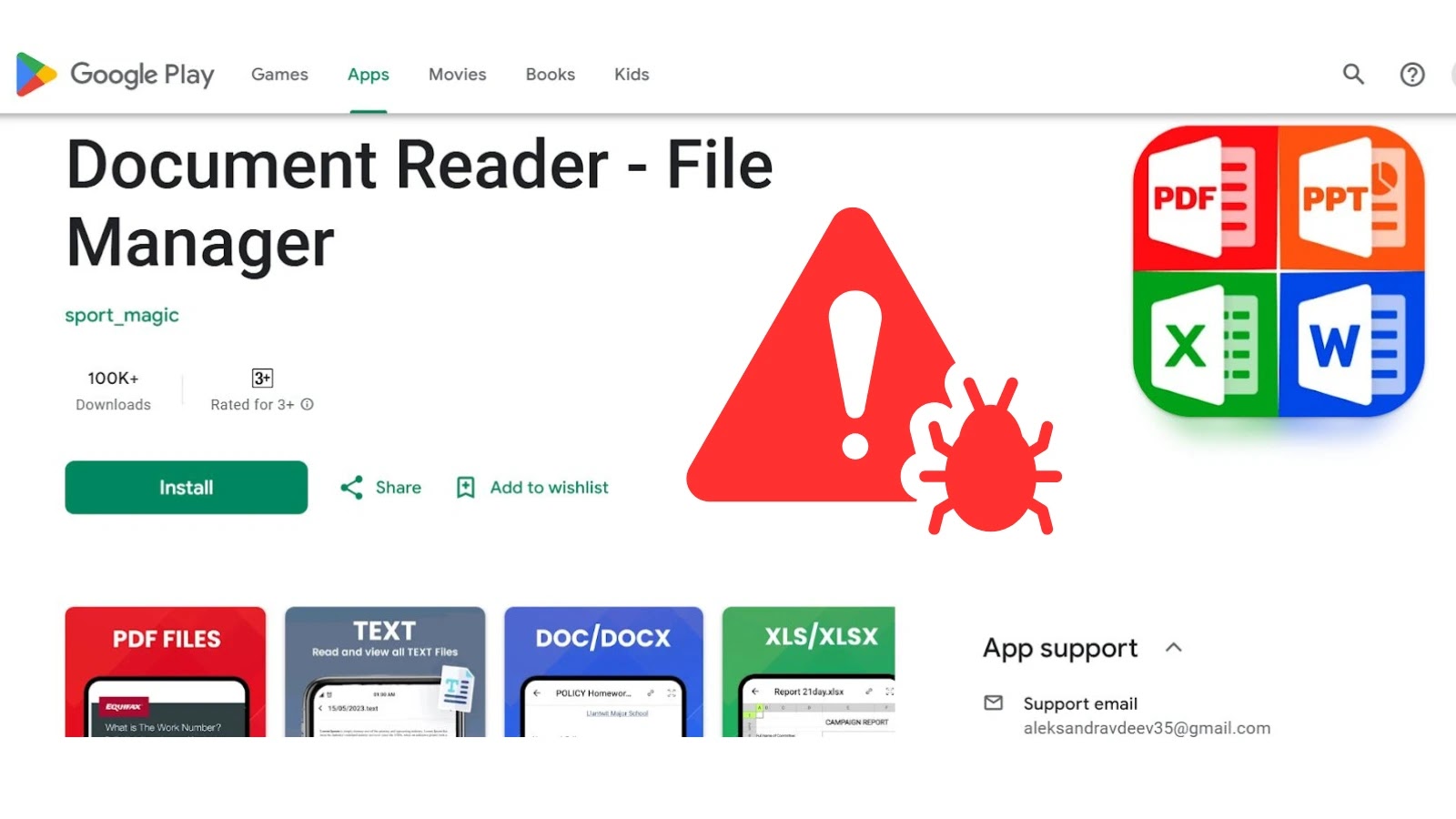
According to the Zscaler Kenencelabz Post shared on X, the malicious application, disguised as “file manager and document player”, worked as a drop-down account, an apparently benign application that recovers and installs additional useful loads from remote servers.
The application has prompted users to download a fraudulent “update” pretending to be an additional module necessary during installation. This update, hosted on the GitHub standards, contained the Anatsa bank Troy.
Anatsa uses an execution of code based on reflection to dynamically load the Dalvik executable Dalvik (DEX) files, which escape static analysis tools denounces the useful charges only at the time of execution.
The malicious software performs anti-emulation checks to detect Sandiny environments, delaying malicious activity until it confirms a real device. Once active, he requests critical authorizations, in particular:
- Accessibility services: To save strikes, intercept SMS messages and handle screen content.
- Access to SMS: To bypass the two -factor authentication mechanisms (2FA)
The Trojan then establishes communication with the command and control servers (C2), to transmit metadata from the system and to receive targeted bank applications profiles.
For each financial application detected (for example, Paypal, HSBC, Santander), Anatsa injects a superposition of counterfeit connection, capturing the identification information directly of users without distrust.
The latest Anatsa campaign has mainly targeted users in Europe, including Slovakia, Slovenia and Cheche, although its infrastructure supports expansion in the United States, South Korea and Singapore.
The target list of malware includes more than 600 banking and cryptocurrency applications, allowing threat actors to carry out a fraud on devices (ODF) by launching unauthorized transfers via automated transaction systems (ATS).
Attenuations
To mitigate risks, users must:
- Avoid the key load: Disable “Install from unknown sources” in the device settings.
- Audit application authorizations: Revoke accessibility and access to SMS for non -essential applications.
- Monitor for updates: Legitimate applications update via official stores, not third -party links.
The Anatsa campaign underlines persistent shortcomings in the safety of app stores, in particular with regard to delayed attacks in payload.
Although Google has deleted the identified droppings, similar threats remain widespread, often operating file managers and public service applications to escape suspicion.
For end users, vigilance and adherence to basic safety hygiene remain critical defenses against the evolution of mobile threats.
Compromise indicators (IOC):
Network:
hxxps://docsresearchgroup[.]com
http://37.235.54[.]59/
http://91.215.85[.]55:85
Example of MD5:
a4973b21e77726a88aca1b57af70cc0a
ed8ea4dc43da437f81bef8d5dc688bdb
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free